How Rob Monster Took Control of the Alt-Right’s Online Infrastructure and Betrayed It
“I believe all lemons are for lemonade,” said Rob Monster, CEO of Epik, during a live Q&A video conference after being asked if he viewed the hacking of his customers’ data as ultimately being beneficial for his company. Mr. Monster went out of his way to become responsible for safeguarding the alt-right’s web presence by misrepresenting his company Epik’s products and services, and ended up callously hurting a lot of people, while making Mr. Monster tens of millions of dollars in the process.
Mr. Monster spent nearly four hours on the video conference discussing the data breach and a wide range of unrelated topics before an audience of tech journalists, hackers and internet trolls. During that time, Mr. Monster admitted that he had not only never bothered to inspect his company’s code before the hack, but didn’t even have access to said code because it was being managed, and possibly even owned, by another company located in eastern Europe. Incredibly, in spite of this gross lack of security, Mr Monster had been guaranteeing his customers that Epik was the “Swiss Bank of Domains” and their very personal data was safe with him. However, the only assurance Mr. Monster gave his customers after the hacking of all their data was to inform them that he and his team of cyber security specialists had been busy putting curses on the data, which he claimed would cause the hard drives of anyone who opened the data with malicious intentions to burst into flames.
Also during the call Mr. Monster attempted to bribe several journalists and hackers to get them to stop speaking poorly about Epik in exchange for deplatforming one of his customers and associates, Joey Camp, an internet investigator and troll who Mr. Monster had previously used to harass a wikipedia editor and her family because he disagreed with the wiki entry she made about Epik. From here on out, the call spiraled into discussions ranging from Mr. Monster’s masturbation habits to his love of billionaires and the neo-nazi troll Weev, a known ten year associate of billionaire Peter Thiel and Jeff Gisea.
Mr. Monster’s video conference did little to give more information on the hack, however all one has to do is look at his past statements and behavior to understand that this situation was a long time in the making. Mr. Monster has a long history of making false statements regarding his products and services, with little to no regard for the privacy and security of his customers. For example, Mr. Monster had for years before the hack claimed to have his own VPN service, which was revealed to actually be a simple white label of another company’s product that he had no direct control over. Mr Monster had also previously been caught using false marketing infographics, stolen from a competitor to show how powerful his DDoS service was. When he was confronted with these false claims he first tried to ignore and dismiss the claims and then accused those that reported on the story of lying, threatened to sue them and tried to get them censored from various social networks. Mr. Monster was made aware of Epik’s vulnerabilities months before the hack, however Monster responded in typical fashion by ignoring and dismissing the claims, and then when the evidence became overwhelming he started to attack those reporting on the story and tried to silence them by getting them removed from social networks all while the problems went unfixed1.
Mr. Monster’s actions before and after the hack range from grossly incompetent to malevolently subversive. In the years leading up to the hack, Monster would go out of his way to aggressively market and cater to alt-right websites, most notably conservative social media site Gab. Despite assuring his far right customers that their data was safe with Epik, the self-described “Swiss Bank of Domains”, the hack not only revealed his customers’ personal information, domain names, and credit card numbers, but also revealed website server credentials for all the websites hosted at Epik, thereby giving the hackers direct access to all of those other websites and their users’ data; Texas GOP, Oathkeepers, and Proud Boy websites to name a few.
Epik initially denied knowledge of any hack after it had first been widely reported on in the media2. Two days later Epik sent an email to customers that alluded to an “alleged security incident”3. Customers were officially informed about the hack by Epik on September 194, six days after the data was posted publicly and three days after Monster’s video conference informing journalists and internet trolls of the situation. Since the hack, Mr. Monster has enjoyed an increase in publicity and even boasted of gaining more business than losing since the hack, all the while his customers suffer the consequences ranging from being harassed by Antifa activists, to losing their jobs and some even being prosecuted.
The other very interesting revelation that came out of Monster’s live call, besides his utter lack of concern for those he had hurt, was the fact that he had received a $32,000,000 “investment” just a couple months, maybe weeks, prior to the hack, for a minority share of Epik, with no board seat. This would give Epik a $64,000,000 valuation, which is pretty incredible considering Epik is a 10 year old company that was not profitable and probably does less than a million per year in revenues. We will discuss this and speculate on who the investors are and what their motives were later in the article.
Monster’s Origins
Before his foray into the world of alt-right online notoriety, Mr. Monster got his start in the corporate world. According to Epik’s now-deleted management team page, Mr. Monster studied Life Sciences and Economics at Cornell University and worked for Proctar and Gamble for eight years5. He left the company in 1999 and founded GMI Inc, a market research company. According to Mr. Monster, the company experienced rapid growth, but due to bringing in outside capital, he was forced to answer to a board of directors, which he viewed as “a necessary evil”. In 2007, on account of being “unwilling” to manage the board, Mr. Monster was deposed as CEO in what he described as an “initiative by an activist board member”6. He then went on to serve as CEO of Digital Town and was again removed as CEO three years later.
Around this time, Mr. Monster claimed to have become a born against christrian6 and would often hide behind his religiosity when confronted with his false claims about his products and services, which would often escalate into him making threats and attempting to silence those who expose him, as he would later demonstrate during the fallout from the Epik data dump.
Epik was founded by Monster in 2009 as a domain name asset development company7b with the goal of “being the domainer’s best friend”8. The company initially profited off of the way google prioritized a site’s domain name in its algorithm, before a change in 2010 “trashed their business model”. Losing revenue and needing to change business models6, Monster bought Intrust Domains in 2011, inheriting its code and development team7b. This enabled Epik to offer registrar services and began its pattern of acquiring companies to offer their services under Mr. Monster’s name and brand. Epik would go on to offer virtual private network, denial-of-service protection, and web hosting services through its acquisitions of Anonymize, Bitmitigate, and Sibyl Systems, respectively9, whose shady histories we will examine in greater detail in the next section.
Although Epik prided itself on its “legendary customer service”6 and being the self-described “Swiss Bank of Domains”, they were struggling financially but were able to attract some early investors like Braden Pollack10 and Tal Moore11, who were both made members of the board as well.
In March of 2020, Epik hired Robert Davis, a teen prodigy who got his start working with the National Security Agency and Navy Intelligence in cryptology13. As of 2022, Epik is the 22nd largest domain registrar with more than 700,000 domains registered14.
Becoming the Alt-Right’s Cyber Guardian
Mr. Monster’s, and by extension Epik’s, association with the American Dissident Right began in earnest in 2018 following the aftermath of the Pittsburgh Synagogue shooting. The alleged shooter, Robert Bowers, was a regular user of right-wing twitter competitor Gab. On October 27, he made a final post blaming Jews for mass migration, ending with “Screw your optics, I’m going in.”, referencing the post-Charlottesville optics debate that the alt-right was having at the time. Two hours later Bowers allegedly shot and murdered nearly a dozen jews in the Tree of Life Synagogue in Pittsburgh, Pennsylvania15.
As a direct result of the shooting, Gab’s domain provider GoDaddy stopped providing its service due to “instances of content on the site that both promotes and encourages violence against people”, which left Gab inaccessible to users16. During this time, Mr. Monster claimed he was following the situation and wondered why GoDaddy would discard a $300,000 domain name. Mr. Monster reached out to Gab’s founder and owner Andrew Torba and agreed to take Gab on as a customer. Despite the controversy that this action would bring, Mr. Monster would later attribute taking on Gab as reinspiring him to focus his time running Epik7c.
Following his association with Gab, Monster said Epik was presented with many opportunities that came to them. One of these opportunities came about in early 2019 with the acquisition of Bitmitigate, a cybersecurity company that offers website protection7d. Bitmitigate was infamous in its own right before being acquired by Epik due to its providing DDoS protection to the neo-nazi website The Daily Stormer. In circumstances very similar to how Mr. Monster reached out to Mr. Torba, Bitmitigate’s founder Nicholas Lim personally reached out to Andrew Anglin, owner and publisher of The Daily Stormer, after it had been dropped by Cloudflare following the disastrous 2017 Unite the Right rally. Unlike Mr. Monster, however, Mr. Lim provided service to The Daily Stormer free of charge17. Under Mr. Monster’s ownership Bitmitigate eventually stopped providing services to the neo-nazi website, apparently due to Mr. Monster being unaware that it was a customer. Mr. Monster described the situation as “regrettable” due to the negative baggage the Stormer brought18, which is odd considering how friendly Mr. Monster was with Weev, the Daily Stormer’s Chief Technical Officer, during his hack response video conference in 20217e.
Mr. Monster acquired Lim’s company, Bitmitigate, and named Lim Epik’s Chief Technical Officer. Mr. Lim’s time at Epik did not last very long; in 2019, after 8chan was adopted by Epik following the fallout from the Christchurch mass shooter posting his manifesto onto one of its message boards. This proved too much for Voxility, the company Epik had been renting web space from, which resulted in Epik itself being dropped from their service19. Epik then stopped providing service for 8chan, due to the “concern of inadequate enforcement and the elevated possibility of violent radicalization on the platform”20. Shortly thereafter Mr. Lim left Epik to start a new company. Curiously, when Bloomberg Businessweek emailed Mr. Monster asking about Lim’s role at Epik, they received a reply from Epik’s senior vice president of communications Robert Davis, who wrote that Mr. Lim had only been a short-term consultant19.
Sibyl Systems was another Epik acquisition that was even shadier than Bitmitigate. Sibyl was incorporated in 2017 in the Seychelles, thus hiding its corporate ownership, and is managed remotely by an international team that ended up simply being a handful of literal teenagers in the United Kingdom hosting lolicon and other questionable content on a couple rented servers, making less than a couple thousand dollars per month in total revenues. Sibyl provided hosting services to Gab after the Pittsburgh shooting and was later acquired by Mr. Monster in 2019 who labeled it as an Epik service.
It was around this time that Monster’s burgeoning association with the alt-right began to cause some of Epik’s original employees and investors to jump ship. Board member and investor Tal Moore disassociated from Epik almost immediately as a result of the company’s association with Gab21, while Braden Pollack, resigned from the board later in June of 2020, citing that he and Monster did not share “the same ideology” anymore22. Epik’s director of operations Joseph Peterson, who had worked at Epik since 2017, quit after the 2019 Christchurch Mosque shooting after Monster showed a video trying to convince his staff that the shooting was fake. Mr. Peterson, who shared Monster’s view that domain registrars shouldn’t discriminate against clients based on ideology, told Bloomberg that by this time Mr. Monster’s political agenda was dominating Epik’s company culture21.
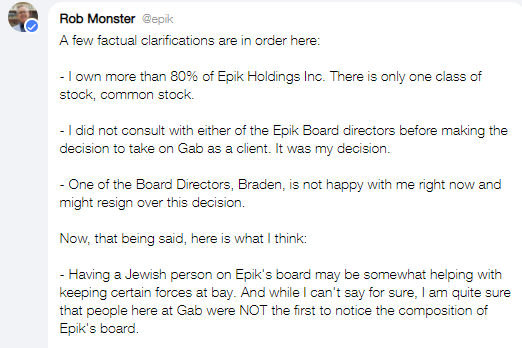
Mr. Monster’s association with the alt-right went beyond simply providing web services; he actively interacted with many users from the alt-right, ranging from major e-celebs to anonymous Gab trolls. An early example being shortly after Mr. Monster created his @epik account on Gab after taking it on as a customer, he was quickly accused of being a “RAT KIKE” by a user. Monster responded that he was not a “’ kike’” and wrote that having Jews on Epik’s board may help keep “certain forces at bay”21.
The following year in early January, 2019, Mr. Monster took a step beyond interacting with users on Gab by appearing on an alt-right podcast hosted by former Daily Stormer writer Eric Striker. On the podcast, Mr. Monster praised former KKK Grand Wizard David Duke as being “clever” and “articulate” despite not knowing “the body of his work”. After his appearance Mr. Monster claimed to have not known who Eric Striker was nor that the interview was being recorded for broadcast29.
Monster would also on occasion interact directly with alt-right e-celebs on Gab. Shock jock Christopher Cantwell of Charlottesville infamy caught Mr. Monster’s attention in particular. After Mr. Monster brought Gab back online, Mr. Cantwell made a vaguely threatening post regarding Hilary Sargent, a known critic of both Cantwell and Gab. After a few days of Ms. Sargent pestering Mr. Monster to do something, he reached out and personally asked Mr. Cantwell to remove the post, which he did. Mr. Cantwell appeared to have received Mr. Monster positively, writing “Woe to us if we do not earn his loyalty” and Mr. Monster wrote that Mr. Cantwell was “thoughtful” and “theatrical”29.
Concurrently, Mr. Monster privately texted a leftist journalist, Molly O’Shah, on twitter, telling her that he was “on to Cantwell”, who was the first on his list to be kicked off of Gab and that he had Mr. Torba’s ear to do it. Along with the unsolicited message Mr. Monster attached a screenshot that had Cantwell’s phone number unredacted on it. When asked, Mr. Monster told Mr. Cantwell that he was trying to set up a debate between him and Ms. O’Shah. After days of trying to understand Mr. Monster’s behavior Ms. O’Shah concluded that Gab was a honeypot30. Mr. Cantwell was banned from Gab less than a year later31.
Mr. Monster didn’t just interact with his new eccentric, right-wing audience; he employed some of them, too. Joey Camp was a client of Epik’s who ran a research/doxing website called YourDaddyJoey.com, which Mr. Monster described as being in the business of “outing bullies and thugs”, despite admitting later that Mr. Camp also behaves like a bully. Mr. Monster admitted to using Mr. Camp’s services as a “world class investigator” to “track down a guy” for allegedly benevolent purposes. Mr. Monster claims that Mr. Camp found him, although he didn’t agree with some of his questionable operating methods7g. This would not be the last time Monster would be in need of Mr. Camp’s services.
As a result of taking on Gab as a customer and using them as marketing, Epik went on to provide its services for the American Dissident Right’s most notable and popular websites like Bitchute, AR15.com, Patriots.win23 as well as for activist groups like the Proud Boys24, Oath Keepers25 and Atomwaffen Division26 and most notably Alex Jones’ Infowars.com.
Despite claiming not to know or have ever spoken to Mr. Jones, Mr. Monster described Infowars as “the gateway drug to the truth” and even had an affiliate partnership with Infowars. Several months prior, in April of 2021, Mr. Monster posted a short segment from Mr. Jones’ show in which he declared that Infowars “wouldn’t be around if it wasn’t for Epik” and praised it as being “the only true domain registrars, not a reseller”. Mr. Jones then plugged infowarsdomains.com to his listeners, which redirects to epik.com, to get “the lowest prices” on moving and registering domains, “protected systems”, and “all the services you need”. Mr. Jones ended the pitch by telling his audience that they were “insane” for registering their site anywhere other than Epik and that a percentage of the sale goes to Infowars27.
During the segment Mr. Jones called Epik “big fans” of Infowars and mentioned that it was headhunting some of his employees. Mr. Monster ended up hiring Infowars’ director of IT Michael Zimmerman to work for Epik7f, who has been alleged to also be providing tech support for Nick Fuentes’ America First youth movement26. Mr. Zimmerman was made Epik’s director of enterprise service, and later it was uncovered that Mr. Zimmerman and several of his fellow Epik employees registered websites venerating the Christchurch Mosque shooter Brenton Tarrant like “Sainttarrant.com”, “shooterchan.com”, and other domains based on accelerationist alt-right memes like “Right Wing Death Squads”28.
In under three years, from when Epik took on Gab as a customer in Fall of 2018 to getting Alex Jones to shill Epik’s services to his millions of listeners in the Spring of 2021, Mr. Monster had consolidated his hold over a good portion of the American Dissident Right’s web presence. Domain registering, hosting, DDoS protection, virtual private network service; all the services an alt-right net denizen would need, all available at the same place from Epik, “Swiss Bank of Domains”, and under the care of vocal professing christian libertarian Rob Monster. At this time the threat of the Dissident Right getting deplatformed off the web had been averted, little did they know that consolidating under Epik would expose them to a cyber threat much worse than just simply getting deplatformed.
#EpikFail
As the trials for the January 6 Capitol protests began heating up, almost on queue, Epik was hacked and all of its user data was published online. Hacktivist collective Anonymous took credit for the hack, though known Fed asset and self-described founder of Anonymous, Aubrey Cottle, would later take full responsibility58. Once the raw data had been dumped it was sorted and distributed by “Demon Hacker” Emma Best’s DDoSecrets, the same website that handled Gab’s data when it was hacked in February and March of 202159. Important to note that some have claimed the hack is ongoing and Gab data is still accessible to anonymous and their employers.
In January of 2021, cyber security researcher Corben Leo discovered a major vulnerability in Epik’s code. Mr. Leo had found a library on Epik’s Whois page that was susceptible to an old hack that allowed anyone to remotely run code on an internal server without a password. Finding out that this hack gave him access to Epik’s internal server, Mr. Leo attempted to contact Mr. Monster via linkedin to ask how to report the bug to Epik. Mr. Monster, despite boasting his hands-on approach to Epik’s “legendary” customer service, never responded to Mr. Leo’s message. Mr. Monster later admitted that he had received Mr. Leo’s message, but claimed he assumed he was a bounty hunter before dismissing the message as “linkedin spam”. When asked after the hack, Mr. Leo speculated that this vulnerability is how Anonymous was able to hack Epik and that it has since been fixed32.
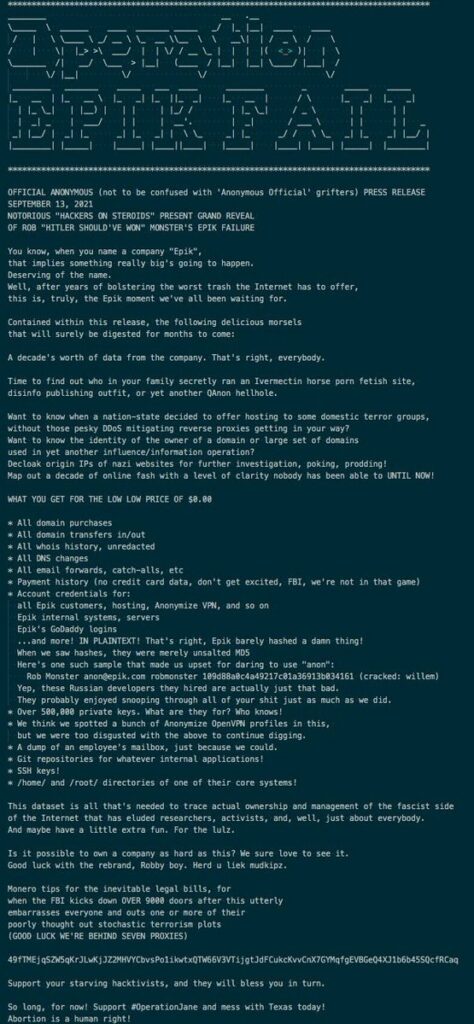
Over half a year later, on Monday, September 13, Anonymous put out a press release announcing that they had come into possession of a decade’s worth of data from Epik. Dubbed ‘Operation Epik Fail’, the release explained that Epik had for years been “bolstering the worst trash the internet had to offer” and the leaked data now made it possible to identify the owners of domains they found disagreeable. Some of the types of leaked information included domain purchases and transfers, unredacted Whois history, payment history, account credentials, private keys, Epik’s VPN profiles, which may have included web history, and much more. Anonymous also referenced hired Russian developers who were responsible for Epik’s abysmal security and showed the username and password for Mr. Monster’s Epik email account. The release repeatedly emphasized using the data to expose the “ownership and management of the fascist side of the internet”34, i.e. Mr. Monster’s customers.
According to the Daily Dot, journalist Steven Monacelli was the first to break the story on Anonymous’ release. Four hours after tweeting a screenshot of the release on twitter, Mr. Monacelli posted screenshots of his newly hosted dox on Mr. Camp’s website, who Mr. Monacelli immediately linked to Mr. Monster and Epik via its Whois record. The dox contained Mr. Monacelli’s picture, phone numbers, employment information, allegations that he was a pedophile, and promises to post family and financial information. The text also accused Mr. Monacelli of fabricating the screenshot with Mr. Cottle to push a hoax to “hinder the commercial and business of Epik”33.
Along with the screenshots, Mr. Monacelli quote tweeted Mr. Monster posting the dox of someone else who was reporting on the hack, which was also hosted on Mr. Camp’s website. Mr. Monster then replied to Mr. Monacelli’s tweet, claiming no knowledge of who he was other than that he had been interviewed by him over a “nothing burger” story a week prior34. As the release was getting more and more mainstream media attention, Gizmodo contacted Epik asking for a comment, a spokesperson answered via email: “We are not aware of any breach. We take the security of our clients’ data extremely seriously, and we are investigating the allegation.”35
While Mr. Monster ignored the release and engaged in twitter drama, Anonymous was preparing to disseminate the hacked data in an accessible format. The following day, Tuesday, September 14, Anonymous made 180 gigabytes of the hacked data available on epikfail.win33. The same day, Anonymous hacked Epik’s support page, creating a post mocking Epik for being stupid enough to allow the hack to happen and referred to Epik’s customers and employees as all “fascists, pig-fuckers, al-Qaida child porn loving nazi assholes”. The post also gave a link to the stolen data.35 37
Within a day the hacked data was verified by the media. A computer engineer hired to evaluate the hack by an Epik customer told The Daily Dot that Epik was “fully compromised” and that the hack was the worst he had ever seen. He explained that the hacked data consisted of Epik’s primary database of plaintext, unencrypted usernames, passwords, WordPress login credentials, SSH keys, and credit card numbers; information that hackers could use to completely take over the websites of countless Epik customers1. Also included in the data were employee emails, private keys, and SQL databases with customer records for Epik’s domains, thereby enabling anyone with access to the data to identify which Epik domain is owned by which customer39.
The victims of the hack were not limited to just Epik’s customers. Through acquired subsidiary Anonymize, Inc, Epik offered users free privacy proxy services to “cloak” domain owners’ identities from the Whois database, which did nothing to protect them from Mr. Monster’s “carelessness”, as 15 million email addresses of Epik customers and even non-customers were released as part of the breach. Due to Epik scraping Whois data, even the email addresses of non-customers were included in the data dump, potentially opening them up to doxxing, harassment, and reputation loss due to being associated with Mr. Monster40.
On Wednesday, September 15, Mr. Monster sent Epik customers an email mentioning “an alleged security breach” that Epik’s internal and external teams were working on fixing, thanked his customers for their support and prayers, and stated his belief that God will turn the evil of the hack into good41. Neither Mr. Monster nor Epik made any further statements about the hack until Thursday, when Mr. Monster hosted a live public video conference to address the hack.
Running over four hours long, Mr. Monster initially kept the conference on the topic of the data breach. Mr. Monster claimed that Anonymous had only gotten a backup, which he downplayed as not being as bad as them having access to a live system. The chat accused Mr. Monster of being in denial, which he denied, claiming he was waiting to make a formal statement to customers after more review7h. A user in the chat named “Frustrated Customer” would later ask Mr. Monster if Epik would fix the hack, to which he reiterated: “I don’t believe there was a hack of our core system, I believe that somebody got access to an old backup.” Mr. Cottle, who would later join the conference but deny anything to do with the hack42, expressed doubt over Mr. Monster’s backup excuse, as there were active credentials and keys that allowed access to Epik’s main network43.
Journalist Mikael Thalen asked in the chat about plaintext credit card information featured in the data breach. Mr. Monster said he was “mystified” and claimed that Epik only stored the last four digits unless there was “caching going on”, which he described as “bad form, shouldn’t happen.”7i
Mr. Monster then segwayed into briefly explaining Epik’s business model of acquiring other companies and rebranding them as his own and that he had recently received significant funding, $32,000,000, from a “pro-freedom” billionaire in exchange for a minority stake of common stock with no board seat7j. Later in the conference, Mr. Monster told a story of a “prophetic friend” who told him that two billionaires were coming to Christ and would give him the money that he needed. Mr. Monster then claimed to have soon received the $32 million dollars from one of the billionaires7k, who to this day remains unknown to the public.
Mr. Monster went on to admit that he had never inspected his company’s code. Mr. Monster explained that when Epik acquired Intrust Domains in 2011, he inherited the company’s Russian development team and their code. When pressed by the chat, Mr. Monster had to admit that he “bought shitty Russian code” and never got around to evaluating it.7L Upon inspecting the code after the hack, Mr. Monster determined that it “sucked”7m.
Mr. Monster claimed that the hack had nearly broken him, but assured his customers that he and his cybersecurity team had put literal curses on the data and warned the hackers that if they didn’t delete the dataset then their laptops would catch fire7m.
After about an hour the conference devolved as Mr. Monster focused more on interacting with journalists, hackers, and trolls than addressing the hack. Mr. Monster was confronted by Mr. Monacelli over Mr. Camp harassing and doxing him while being hosted by Epik. After a back and forth, Mr. Monster agreed to immediately drop Mr. Camp’s doxing site from Epik’s services as a thinly veiled gesture of good faith in exchange for better coverage7n.
Afterwards, CTO of the Daily Stormer, Andrew Aurenheimer, AKA Weev, joined the call to Mr. Monster’s great interest. Over the past decade Weev had gained the reputation of being one of the most vile figures in the American far-right scene, notably printing flyers calling for the genocide of non-white children to tens of thousands of printers across the country, to name but one of his major trolling operations44. Despite claiming to not know much about him, Mr. Monster immediately engaged with Weev, wishing him “much love” and asking “what’s your why” to explain his views42, with Mr. Monster showing Weev more “love” and attention in ten minutes than he gave to his own customers over the past few days since the hack was first announced. As time went on the video conference degenerated even further, with Mr. Monster discussing subjects ranging from his views on scarcity economics, to if God watches people masturbate, to his personal pornography habits7o.
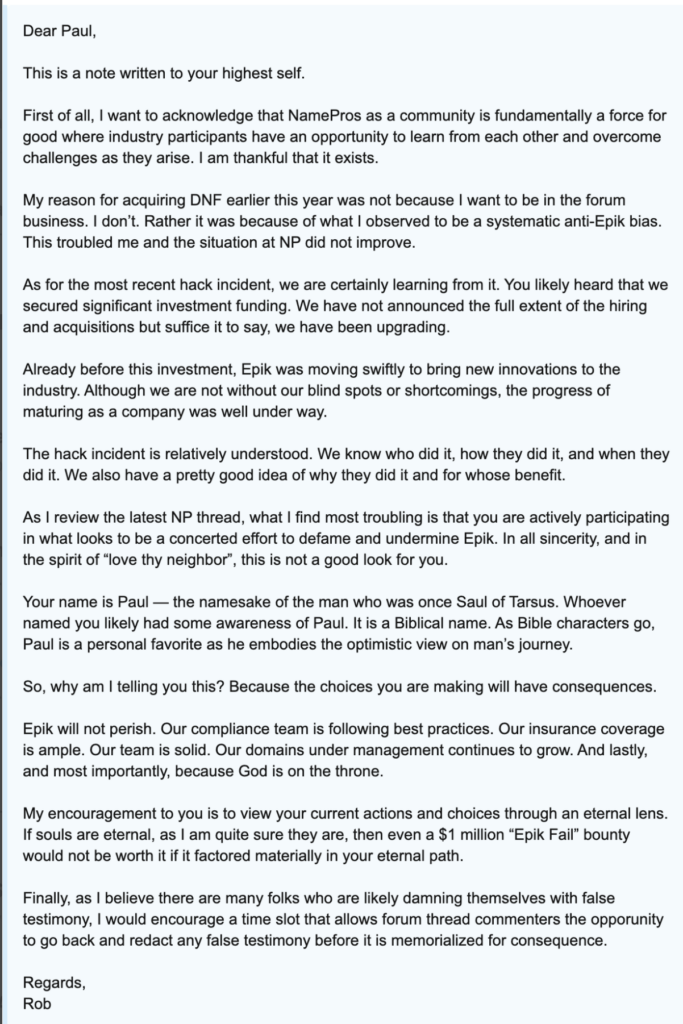
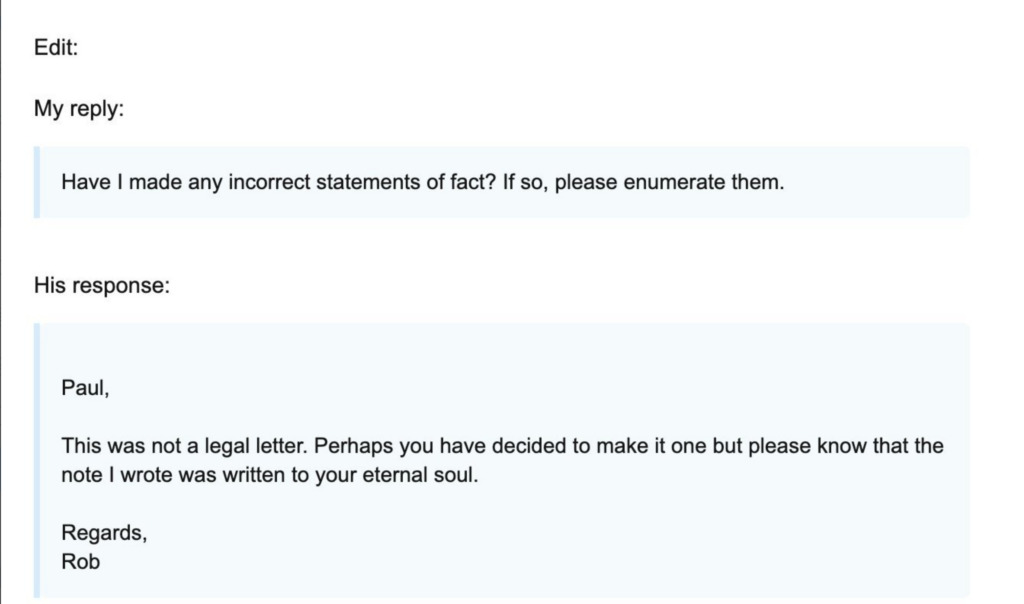
The video conference evidently didn’t have the effect Mr. Monster intended, as in the weeks following the hack he preoccupied himself with squashing criticism against himself and Epik. Molly White, a wikipedia editor who was responsible for updating Epik’s wiki entry, tweeted on September 18 that Mr. Camp was harassing her and her family from his website’s email account, which was still online despite Epik cutting off its services the day before46. Later in the month, Mr. Monster would personally become involved in quashing “anti-Epik bias” by sending several messages filled with religious rambling and thinly veiled threats to Paul, the CTO of NamesPros, a forum dedicated to domain investors, where much of the Epik hack discussions were taking place. In his message, Mr. Monster accuses him of participating in “anti-Epik bias” in the forums to “defame and undermine Epik” and encouraged Paul to “redact any false testimony before it is memorialized for consequence”. Paul replied asking what incorrect statements were made and Mr. Monster ignored the question, instead replying that his message was not a legal threat but rather a letter written to his “eternal soul”47.
The day after the conference, September 17, Epik posted in a now-deleted tweet officially confirming that a breach had occurred and claimed that it had been identified and was in the process of being fixed45. Another email to customers was sent on the 19th, which finally addressed the hack. The email urged customers to “remain alert for any unusual activity they may observe regarding their information used for our services – this may include payment information including credit card numbers, registered names, usernames, emails, and passwords”40. This wasn’t the end of the ordeal, however.
Ten days later, Anonymous released more hacked data, this time a 70 gigabyte torrent file containing several virtual disk images of Epik’s entire systems. The Daily Dot reached out to a cybersecurity expert who had reviewed the second leak to explain that it included Epik’s “entire server image, with all the programs and files required to host the application it is serving” as well as API keys and login credentials for Epik, its company twitter account, and other sites such as Paypal and Coinbase. This time, however, Mr. Monster didn’t respond to requests for comment48. A few days after that, on October 4th, Anonymous released a third and so far final data dump. The data consisted of additional bootable images of Epik’s servers and data from the Texas Republican Party’s website, which was also hosted by Epik49. Monster issued a statement on the first data release but did not issue any statements on the second or third releases and as of publishing this article neither has he offered any sort of apology nor even seemed contrite in any way for the harm done to his customers.
Epik Fallout
According to a data-breach notice filed by Epik with Maine’s attorney general, 110,000 people had their financial information put at risk as a result of the breach51. The damage brought about by the data breach wasn’t just limited to the risk of credit card fraud; many victims lost their jobs, peace of mind, and even their freedom as a result of the “Swiss Bank of Domains” lacking to live up to its name.
The data dump was described as a Rosetta Stone to the Dissident Right, giving researchers information that they could only dream of acquiring legally. The mainstream media was reporting as early as late September that the owners of right-wing websites and domain names were being identified. The Washington Post reported that one Epik customer was fired from his job after his name was found in the data to be the owner of theholocaustisfake.com and other similarly far-right themed domain names50. Other, less scrupules actors made twitter accounts dedicated to posting doxes on the purported individuals behind websites like the Proud Boys forum51.
Epik’s data breach proved to be a boon to January 6 investigators, as many of the core groups involved in the Capitol Riot had their websites entrusted to Mr. Monster. The Oathkeepers, the right-wing militia group considered to be central figures in the January 6 Protest, had 5 gb of their data leakedafter the main Epik dump, revealing over 10,000 emails from members and chapter leaders, an archive of their chat service, and a membership list with over 38,000 email addresses. This information was then used to personally identify members and donors as being part of the militia53.
Right-wing e-celeb customers were put under even more scrutiny. Ali Alexander, organizer of the Stop the Steal movement that culminated in the January 6 Riot, was using Epik’s Anonymize service to hide his association with more than one hundred domains registered with Epik. The leaked data contained Mr. Alexander’s Anonymize account’s login information and his unique ID, which the service gives its users to replace their names on the domain registrar. With that unique ID, researchers were able to tie Mr. Alexander to each website he had registered with Epik, 57 of which were associated with the Stop the Steal movement. Mr. Alexander anonymized his name with these sites after January 6th52, ostensibly to downplay his involvement, yet his efforts were for naught due to Mr. Monster’s empty promises of anonymity and security.
Perhaps what can be described as the most insidious consequence of Mr. Monster’s failed promises is how easy he made it for governments to persecute dissidents who were exposed by the breach. Found in the hacked data were subpoenas and data preservation requests of domains from law enforcement, with notes added by Epik to not disclose the request to the customer54. Because of the hack, US law enforcement was able to conveniently acquire data on the Dissident Right without going through the trouble of issuing a subpoena or obtaining a warrant, which they probably would not have been able to acquire. Mr. Monster’s self-professed libertarian and Christian beliefs gained the trust of many dissidents inside and outside the United States, some whose only protection from persecution had been anonymity.
Mr. Monster said during his video conference that the hack had nearly broken him, yet he has yet to face any consequences for his irresponsibility and dishonesty. Mr. Monster saw that there was a possible vulnerability in Epik as early as January 2021 and yet did nothing about it. Mr. Monster continued to shill Epik as the “Swiss Bank of Domains” to a right-wing audience desperate for a sympathetic and safe platform, services whose code he had never bothered to inspect. When given a day’s warning by Anonymous that Epik’s hacked information would be getting leaked Mr. Monster ignored the problem. Even when the information had been posted and Epik’s support page was defaced by the hackers, Mr. Monster couldn’t be bothered to email his customers informing them of the situation until days later at his convenience. Mr. Monster took more action to alternatively placate and silence critics than he did warning his customers of the danger he had put them in.
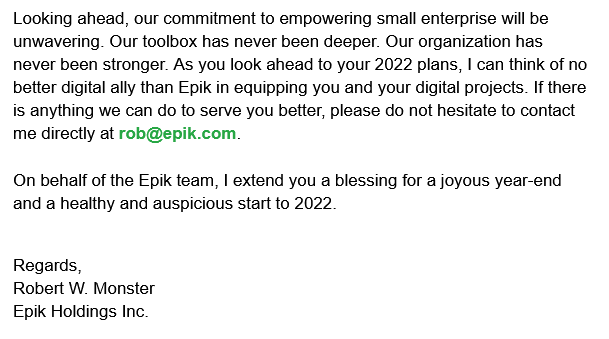
Not only has Mr. Monster so far avoided any consequences from the Federal Trade Commission or his customers, he’s claimed to ultimately have benefited from the hack. During and after the video conference, Mr. Monster boasted of gaining more domains than losing as a result of the hack7m. Things were back to business; in Epik’s December 2021 newsletter, Mr. Monster wrote to his customers thanking them for the “opportunity to be part of [their] 2021” and advertised a new premium cybersecurity service called Cybermarks.com, and made no mention of the hack. Mr. Monster ended the letter telling the reader that Epik has never been stronger55.
MONSTER BONUS
It’s easy to be strong with $32 million dollars from an allegedly hands off billionaire propping up one’s company. Is it a coincidence that Mr. Monster received this seemingly miraculous investment the same year Epik was humiliatingly compromised? Or was the investment really just a bribe to ensure Mr. Monster’s cooperation in the cataloging and ultimately exposing the American Dissident Right?
Currently there isn’t enough public information to positively identify Mr. Monster’s billionaire benefactor, but the small number of publicly right-leaning billionaires helps narrow down to a few possible candidates. While the Kochs and Mercers are known to be large supporters of conservative causes, many details point to Paypal founder Peter Thiel being Mr. Monster’s billionaire benefactor.
Throughout the 2016 election cycle, Mr. Thiel was alleged to have funded several Dissident Right figures through his longtime associate Jeff Giesea. Mr. Giesea has been tied to a guide titled “How to Fund to the Alt-Right”, which was written under a pseudonym associated with Giesea and advocated the use of bitcoin and Mr. Thiel’s Paypal service. Richard Spencer claimed that Giesea donated thousands of dollars to his institute, which led him to accuse Mr. Gisea of trying to subvert the alt-right56. Mr. Monster’s explanation as to how the “donation” came to pass, being reached out to via an intermediary under an ideological guise, is remarkably similar to how Mr. Thiel reaches out to prospective assets through Mr. Giesea.
Mr. Monster’s bizarre friendliness with Weev gives more credence to Peter Thiel being Mr. Monster’s billionaire benefactor. Weev and Mr. Thiel had been working together since at least 2014, when Weev bragged about meeting with Thiel’s “right hand man.” Weev most likely was referring to Mr. Giesea, who Weev also described as a major and well connected “investor providing help to us racists”56. What could be a better help than spending $32 million to keep their websites online indefinitely and maintaining access to all the data.
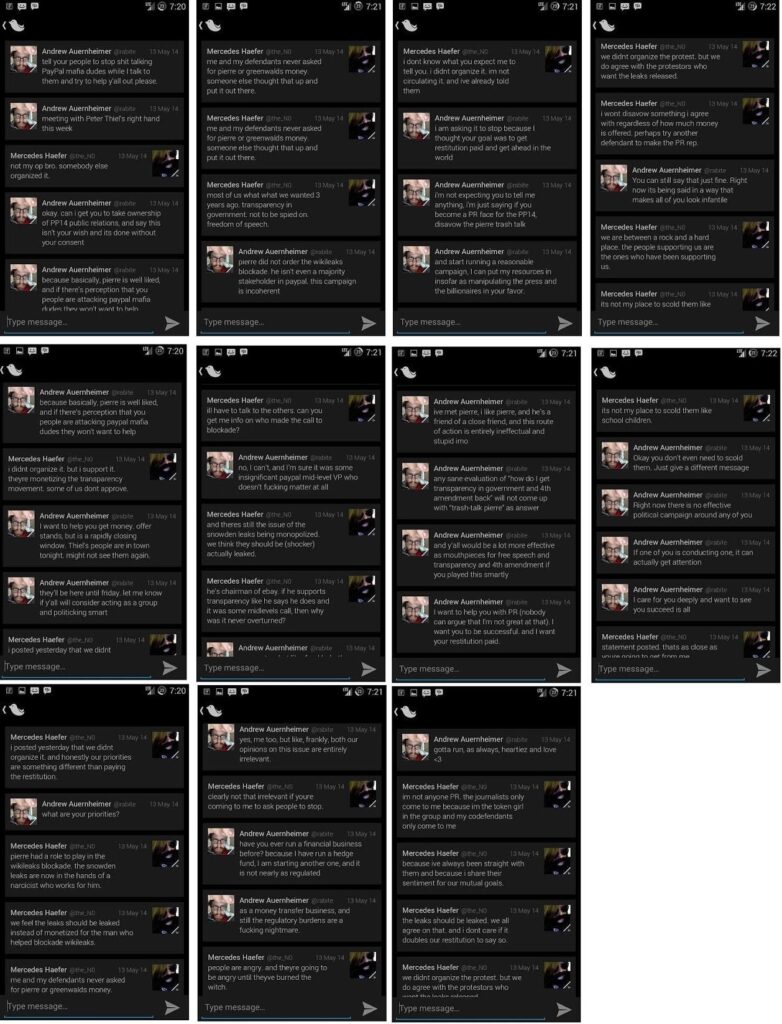
Mr. Thiel’s interest in digital facial recognition and identification would also explain his interest in Epik, which, due to Mr. Monster’s conservative christian affinity grift, was essentially a database of political dissidents’ and their leadership’s real life identities. Mr. Thiel was a driving force behind Clearview AI, a tech firm that scraped social media images into a facial recognition database. Interestingly, Epik also engaged in data scraping of both his customers and non-customers alike. At the same time Mr. Thiel was investing in Clearview, Weev claimed he was working on a “racial” database that used full body images as opposed to just facial data. While Mr. Monster doesn’t appear to share the interest in facial recognition, he does host what essentially is a database of digital identities that can be sorted by ideology. Was the $32 million dollars donated to Mr. Monster to leave a door open for the hackers and ensure that he continues running Epik as a honeypot for the Dissident Right?
CONSEQUENCES OF EPIK PROPORTIONS
After reading this exposé, one might wonder why no major left-leaning news outlets reported on this information in this way in their own reporting on Epik, instead narrowly focusing on the “hate speech” aspect. The answer lies in their motivation: they understand the damage Epik is doing to their ideological opponents and are content with not interrupting their enemy when they are making a mistake. In fact, the leftist media’s reporting on Epik serves as the best possible marketing Epik could ever hope for, since outrage and criticism from the left gives legitimacy to Mr. Monster to many on the right.
If you learn that your community’s bank was robbed,your initial reaction might be to think that’s unfortunate but these things do happen. However, if you later find out that the bank was robbed because the manager left the vault door open, forgot to turn on the security system, forgot to lock the back door on the day of the robbery, and didn’t tell anybody about the heist until after the robbers escaped and bragged to the public about their score, your spidey-senses might start tingling. While it is possible that the robbery was just the result of gross incompetence and unfortunate coincidence, the sheer number of dumb “mistakes” and coincidences would make any reasonable person at least consider the possibility that the robbery was an inside job. In the Epik hack’s case, Mr. Monster was notified that there was an open backdoor into his website, had never reviewed his website’s code and knew nothing about the state of its security, stored his customers’ data, including credit card credentials, conveniently unencrypted in plaintext, and didn’t alert his customers until after their data had already been publicly released. Whether he was in on it or was just a useful idiot, the actions (and inaction) of Mr. Monster was indispensable in ensuring the success of the hack.
The consequences of the Epik hack go beyond some alt-right nazis and conservative boomers getting doxed. While the FBI is able to get subpoenas to request information from a business or website about specific individuals, it isn’t allowed to go on fishing expeditions through entire databases without a warrant in order for the evidence to be admissible in court. The business or website is also unable to voluntarily hand over all of its user data if it violates their privacy policy as it leaves them open to lawsuits by those users who had their personal information revealed. This is why they employ subterfuge. When the FBI wants to get full user data from a website to go on fishing expeditions they use their network of confidential informant hackers, many of whom have been coerced into working with the government because they were caught doing illegal things on the internet, typically involving child pornography or financial crimes. Once a target has been hacked, these hackers turn over the data to “journalists” who in turn publish it on the internet. This method enables the authorities to comb through the data without a warrant and also have it be admissible in court. This appears to be the case for Epik’s hack, as the individual hacker who claimed responsibility was Mr. Cottle, who has admitted on many occasions to regularly workwith the FBI and Interpol61.
The leaking of Epik’s user data for the FBI to peruse coincided with the fallout of the January 6 protests, which came about as a result of Mr. Alexander’s Stop the Steal movement, whose web presence also relied on Epik. Mr. Alexander, an associate of the Thiel network62, corralled the American Dissident Right’s most fervent and active members into the Capitol that day for facial recognition to identify and selectively prosecute those who stand against Mr. Thiel’s vision of the Right, while Mr. Monster did the same thing on the cyber front. It is the opinion of the author that this hack was not just the result of a dishonest grifter who had no regard for his customers but actually an intentional inside job used to gather information on patriots to help authorities prosecute January 6 protestors and anyone else on the right they felt led to prosecute or persecute.
Mr. Monster is an integral part of a much larger network of judas goats, bad actors, and affinity grifters that are currently leading the Dissident Right, likely under the direction of and with the financial assistance from Mr. Thiel, the Mercers, and many others, who will be thoroughly exposed in forthcoming articles.
Here is the entire Rob Monster post hack live stream:
Citations
1. https://www.dailydot.com/debug/epik-hack-far-right-sites-anonymous/
2. https://gizmodo.com/anonymous-claims-to-have-stolen-huge-trove-of-data-from-1847673935
3. https://www.namepros.com/threads/epik-had-a-major-breach.1252094/post-8399304
4. https://www.namepros.com/threads/epik-had-a-major-breach.1252094/post-8399485
5. https://web.archive.org/web/20190510172744/https://www.epik.com/about/management/
6. https://web.archive.org/web/20160819174946/https://www.ppcian.com/a-legendary-interview-with-rob-monster-ceo-of-epik/
7. Rob Monster Video Conference: a. 39:00-39:20 b. 11:26 c. 39:38-41:00 d. 41:00-41:20 e. 1:03:35 f. 1:17:30-45 g. 17:40-22 h. 00:00-2:20, 6:15-30 i. 8:00-20 j. 8:20-9:25 k. 2:10:53-2:12:20 l. 13:49-14:47 m. 1:35:55-1:40:00 n. 44:44-59:38 o. 3:27:40-3:28:20
8. https://www.epik.com/blog/welcome-to-the-epik-blog.html
9. https://www.epik.com/about/labs/
10. https://www.epik.com/blog/braden-pollock-joins-epik-board-of-directors.html
11. https://www.epik.com/blog/amazon-com-cracks-in-the-foundation.html
12. https://www.namepros.com/threads/multi-faith-prayer-request-editable-thread.1163950/page-3#post-7781832
13. Robert Davis Resume Graphic
14. https://www.registrarowl.com/report_registrar_total_domains.php?filter_selected=1&fltr_ctry=1&fltr_tld=&fltr_ctype=1
15. https://www.huffpost.com/entry/robert-bowers-synagogue-shooter-hate-crime_n_5bd4892be4b0a8f17ef84019
16. https://www.theverge.com/2018/10/28/18036520/gab-down-godaddy-domain-blocked
17. https://www.bloomberg.com/news/features/2021-04-14/qanon-daily-stormer-far-right-have-been-kept-online-by-nick-lim-s-vanwatech
18. https://kuow.org/stories/meet-the-man-behind-epik-the-tech-firm-keeping-far-right-websites-alive
19. https://www.bloomberg.com/news/features/2021-04-14/qanon-daily-stormer-far-right-have-been-kept-online-by-nick-lim-s-vanwatech
20. https://www.epik.com/blog/epik-draws-line-on-acceptable-use.html
21. https://www.huffpost.com/entry/rob-monster-epik-gab-neo-nazi_n_5c17bb29e4b05d7e5d846f72
22. https://domaininvesting.com/braden-pollock-resigns-from-epik-board/
23. https://www.npr.org/2021/02/08/965448572/meet-the-man-behind-epik-the-tech-firm-keeping-far-right-websites-alive
24. https://mashable.com/article/epik-domain-names-paypal-proud-boys
25. https://www.buzzfeednews.com/article/salvadorhernandez/oath-keepers-website-epik-down
26. https://www.splcenter.org/hatewatch/2021/11/16/infowars-director-bought-domain-named-after-terrorist
27. https://gab.com/epik/posts/105998298344991991
28. https://www.dailykos.com/stories/2021/11/16/2064684/-Epik-s-hosting-services-provide-connection-for-Jones-Infowars-and-Fuentes-white-nationalists
29. https://www.splcenter.org/hatewatch/2019/01/11/problem-epik-proportions
30. https://mobile.twitter.com/MollyOShah/status/1064559963744419840/photo/1
31. https://www.newsweek.com/social-media-site-gab-bans-crying-nazi-killing-leftists-1367679
32. https://techcrunch.com/2021/09/17/epik-website-bug-hacked/
33. https://twitter.com/stevanzetti/status/1437482759241469958/photo/1
34. https://www.dailydot.com/debug/anonymous-hack-far-right-web-host-epik/
35. https://gizmodo.com/anonymous-claims-to-have-stolen-huge-trove-of-data-from-1847673935
37 https://www.washingtonpost.com/politics/2021/09/17/battle-election-security-funding-is-back/
38. https://www.dailydot.com/debug/epik-hack-far-right-sites-anonymous/
41. https://www.namepros.com/threads/epik-had-a-major-breach.1252094/post-8399304
42. https://www.dailydot.com/debug/epik-ceos-live-video-response-hacking-inciden/
43. https://www.namepros.com/threads/epik-had-a-major-breach.1252094/post-8410406
45. https://web.archive.org/web/20210919005238/https://twitter.com/EpikDotCom/status/1439020408783654917
46. https://twitter.com/molly0xFFF/status/1439285832758726662
47. https://twitter.com/molly0xFFF/status/1443643490093654022
48. https://www.dailydot.com/debug/anonymous-new-epik-leak/
49. https://www.dailydot.com/debug/anonymous-texas-gop-epik/
52. https://www.dailydot.com/debug/ali-alexander-epik-hack-web-domains-capitol-riot/
53. https://www.dailydot.com/debug/oath-keepers-hack/
54. https://www.dailydot.com/debug/epik-hack-subpoenas-data-preservation-leak/
55. https://lowendtalk.com/discussion/176192/terrahost-acquired-by-epik
56. https://www.huffpost.com/entry/clearview-ai-facial-recognition-alt-right_n_5e7d028bc5b6cb08a92a5c48
59. https://www.theverge.com/2021/3/1/22307013/gab-hack-data-ceo-demon-hackers
60. https://www.splcenter.org/hatewatch/2019/02/14/no-way-gab-has-800000-users-web-host-says
61. https://national-justice.com/sites/default/files/2021/10/25/cottle.pdf